Centre de ressourcesGuide pratique
Comment détecter les changements de mot de passe dans Active Directory
Comment détecter les changements de mot de passe dans Active Directory
Audit Natif
- Exécutez GPMC.msc (url2open.com/gpmc) → ouvrez la "Stratégie de domaine par défaut" → Configuration de l'ordinateur → Stratégies → Paramètres Windows → Paramètres de sécurité → Stratégies locales → Stratégie d'audit :
- Auditez la gestion des comptes → Définir → Succès et échec.
- Exécutez GPMC.msc → ouvrez « Stratégie de domaine par défaut » → Configuration de l'ordinateur → Stratégies → Paramètres Windows → Paramètres de sécurité → Journal des événements → Définir :
- Taille maximale du journal de sécurité à 1 Go
- Méthode de conservation pour le journal de sécurité pour Écraser les événements selon les besoins
- Ouvrez l'Observateur d'événements et recherchez dans le journal de Sécurité les id d'événement : 628/4724 – tentative de réinitialisation de mot de passe par l'administrateur et 627/4723 – tentative de changement de mot de passe par l'utilisateur.
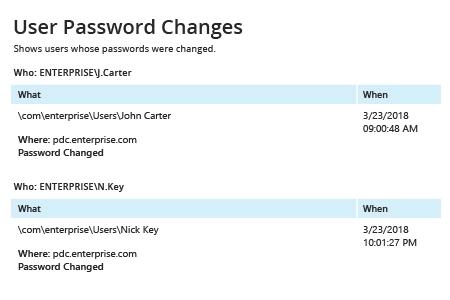
Netwrix Auditor pour Active Directory
- Exécutez Netwrix Auditor → Allez dans « Rapports » → Ouvrez « Active Directory » → Rendez-vous dans « Modifications de l'Active Directory » → Sélectionnez « Réinitialisations de mot de passe par l'administrateur » ou « Changements de mot de passe utilisateur » → Cliquez sur « Afficher ».
- Pour recevoir des rapports par e-mail régulièrement, choisissez l'option "S'abonner" et définissez le calendrier et le destinataire.
Partager sur
