Vulnérabilité Zerologon expliquée : Risques, Exploits et Atténuation
Zerologon est une vulnérabilité de Windows Server (CVE-2020-1472) qui permet aux attaquants d'exploiter une faille dans le protocole Netlogon pour contourner l'authentification sur un contrôleur de domaine. Cela leur accorde un contrôle administratif complet sur un domaine Active Directory en quelques minutes.
Attribut | Détails |
|---|---|
|
Type d'attaque |
Zerologon (CVE-2020-1472) – Élévation de privilèges via MS-NRPC |
|
Niveau d'impact |
Critique |
|
Cible |
Entreprises / Gouvernement / Toutes les organisations utilisant Active Directory |
|
Vecteur d'attaque principal |
Réseau (session TCP vers le contrôleur de domaine) |
|
Motivation |
Gain financier, Espionnage, Perturbation, Extorsion |
|
Méthodes de prévention courantes |
Application en temps utile de correctifs, MFA, application sécurisée du canal Netlogon, EDR, SIEM, surveillance des changements de compte anormaux |
Facteur de risque | Niveau |
|---|---|
|
Dommages potentiels |
Extrêmement élevé |
|
Facilité d'exécution |
Élevé |
|
Probabilité |
Élevé |
Qu'est-ce que Zerologon ?
Zerologon est une vulnérabilité critique de Windows Server (CVE-2020-1472). Elle provient d'un défaut dans le protocole Netlogon Remote de Microsoft (MS-NRPC), où le chiffrement AES-CFB8 utilise un vecteur d'initialisation fixe et entièrement à zéro. Un attaquant a seulement besoin d'un accès réseau de base au service Netlogon d'un contrôleur de domaine (par exemple, via une connexion VPN ou une machine interne compromise) pour envoyer des messages Netlogon conçus pour forcer à répétition la réussite de l'authentification. Une fois réussi, ils peuvent :
- Usurpez l'identité d'un contrôleur de domaine.
- Réinitialisez le mot de passe du compte-machine du DC, même sans nécessiter d'identifiants.
- De là, ils peuvent s'élever directement au statut de Domain Admin et prendre le contrôle de tout le domaine Active Directory.
Cette attaque peut compromettre un domaine Windows entier en quelques minutes, c'est pourquoi Microsoft lui a attribué le CVE-2020-1472 avec un score CVSS de 10.0 (Critique). Le bug a été activement exploité par des groupes de menaces avancées et des opérateurs de rançongiciels, comme Ryuk, Black Basta et Cuba. Corriger cette vulnérabilité n'est pas seulement une recommandation ; c'est absolument critique.
Comment fonctionne Zerologon ?
Examinons chaque étape de l'attaque Zerologon, en comprenant comment un attaquant passe d'un accès réseau de base à la compromission d'un contrôleur de domaine.
1. Établissez une session TCP vers le DC cible
L'attaquant a besoin d'un accès réseau au service Netlogon d'un contrôleur de domaine (TCP/445). Ils l'obtiennent souvent par hameçonnage, des identifiants VPN volés ou un mouvement latéral à partir d'un hôte interne compromis.
2. Initiez un canal Netlogon non sécurisé
L'attaquant exploite une faiblesse cryptographique dans le protocole Netlogon Remote de Microsoft (MS-NRPC). En raison de la faille de chiffrement AES-CFB8 du protocole qui utilise un vecteur d'initialisation (IV) fixe tout à zéro, l'attaquant envoie à plusieurs reprises des messages Netlogon conçus jusqu'à ce que l'un d'eux réussisse avec une clé de session annulée, amenant le protocole à accepter la session sans authentification appropriée. Autrement dit, le protocole échoue à valider la session de manière sécurisée.
Chaque requête élaborée a environ une chance sur 256 de réussir, donc un script peut réaliser l'authentification en quelques secondes.
3. Désactiver la signature & le scellage
Après la poignée de main, l'attaquant désactive la signature et le chiffrement des messages. Cela garantit que le trafic Netlogon ultérieur, y compris les changements de mot de passe, circule en texte clair.
4. Envoyez NetrServerPasswordSet2
Après avoir créé une session Netlogon non authentifiée mais (incorrectement) considérée comme fiable, l'attaquant appelle la fonction RPC NetrServerPasswordSet2 pour réinitialiser le mot de passe du compte machine du contrôleur de domaine à une chaîne vide. De cette manière, l'attaquant prend possession du DC.
5. Exploitez les privilèges élevés
Armé de privilèges de contrôleur de domaine, l'attaquant peut utiliser des outils comme Mimikatz pour effectuer un DCSync.
DCSync abuse du processus de réplication normal que les DC utilisent pour synchroniser leurs bases de données. En se faisant passer pour un autre DC, l'attaquant demande la base de données Active Directory des hachages de mots de passe, y compris ceux des comptes de service et des administrateurs de domaine. Avec ces hachages, l'attaquant peut créer ou usurper n'importe quel compte, maintenir un accès persistant et contrôler entièrement le domaine.
6. Restaurez éventuellement le mot de passe
Certains attaquants réinitialisent le mot de passe du compte machine du DC à sa valeur originale pour éviter la détection de Zerologon tout en conservant l'accès aux identifiants volés.
Diagramme de flux d'attaque
Le scénario d'exemple suivant peut vous aider à comprendre à quoi peut ressembler une attaque Zerologon dans une situation réelle.
Dans un établissement de santé de taille moyenne, un employé du service financier clique sur un e-mail de phishing convaincant, donnant à un attaquant un accès à distance à son poste de travail. À partir de ce point d'entrée, l'attaquant scanne le réseau interne et découvre un contrôleur de domaine non patché. En utilisant la vulnérabilité Zerologon (CVE-2020-1472), l'attaquant établit une session Netlogon de confiance et réinitialise le mot de passe du compte machine du DC à une valeur nulle. Avec les privilèges d'administrateur de domaine désormais en main, ils exécutent une attaque DCSync pour extraire toutes les empreintes de mots de passe Active Directory, se déplacent latéralement vers les serveurs de dossiers patients et déploient un rançongiciel - paralysant les opérations informatiques de l'organisation en quelques heures.
Le schéma illustre une chaîne d'attaque Zerologon typique, de la prise de pied initiale dans le réseau jusqu'à la compromission complète du domaine.
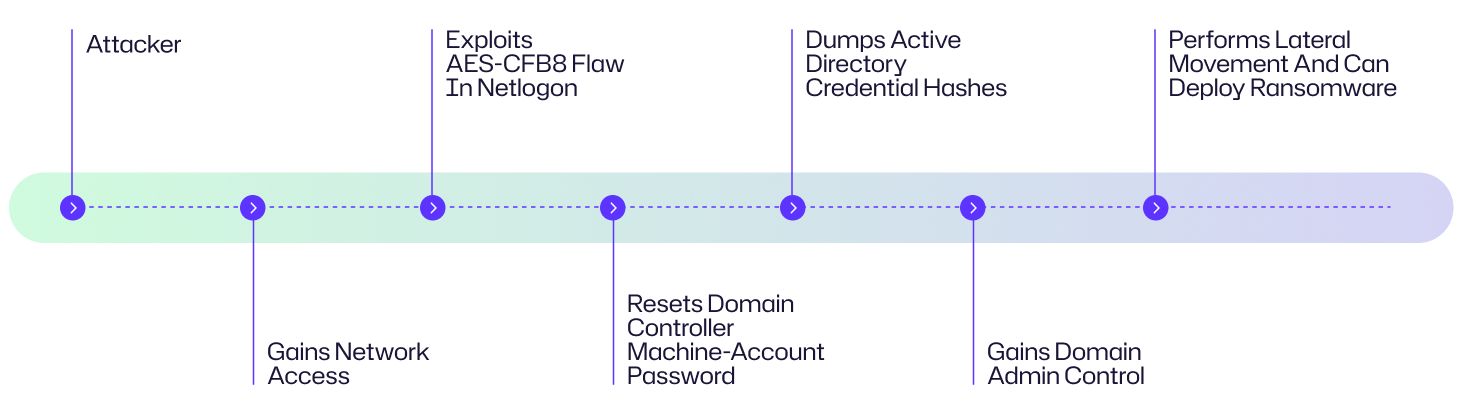
Exemples d'attaques Zerologon
Depuis sa divulgation en 2020, Zerologon a été exploité dans plusieurs violations réelles. Les attaquants ont utilisé cette technique pour mener des opérations de rançongiciel et APT contre des réseaux gouvernementaux, de santé et d'entreprise dans le monde entier. Voici quelques cas réels.
Cas | Impact |
|---|---|
|
Ryuk ransomware (2020) |
Fin 2020, des acteurs de menaces liés au rançongiciel Ryuk ont exploité la vulnérabilité Zerologon (CVE-2020-1472) pour chiffrer des domaines Windows entiers en moins de cinq heures. Les victimes comprenaient des hôpitaux américains et des gouvernements municipaux. Après avoir obtenu un accès initial, les attaquants ont exploité Zerologon pour réinitialiser les mots de passe des comptes machines des contrôleurs de domaine, obtenu des privilèges d'Admin Domaine en quelques minutes, et déployé Ryuk sur l'ensemble des réseaux. Cela a conduit à un chiffrement massif des données, à des perturbations opérationnelles et à des demandes de rançon de plusieurs millions de dollars. |
|
Rançongiciel Cuba (2023) |
En 2023, le groupe de ransomware Cuba a utilisé la vulnérabilité Zerologon (CVE-2020-1472) pour déployer des rançongiciels et exfiltrer des données. Les victimes comprenaient des infrastructures critiques, des services financiers et des fournisseurs de TI. Après avoir obtenu un accès initial, ils ont exploité Zerologon pour réinitialiser les mots de passe des comptes machines des contrôleurs de domaine, obtenu les droits d'administrateur de domaine, puis déployé le rançongiciel Cuba à travers les réseaux. Cela a conduit à des systèmes chiffrés, au vol de données et à des demandes de rançon pour double extorsion, menaçant de publier si la rançon n'est pas payée. |
|
Black Basta |
Le groupe de rançongiciels Black Basta combine Zerologon avec d'autres techniques d'escalade de privilèges pour une prise de contrôle rapide. Après avoir obtenu un accès initial par hameçonnage, ingénierie sociale ou vulnérabilités logicielles non corrigées, les attaquants élèvent leurs permissions en utilisant des exploits tels que Zerologon et des outils comme Mimikatz. Une fois le contrôle au niveau du domaine atteint, les affiliés de Black Basta exfiltrent des données sensibles (souvent en utilisant rclone), désactivent les défenses, suppriment les sauvegardes et chiffrent les systèmes pour une double extorsion. Les victimes incluent les secteurs de la santé, de la fabrication et des services publics. À partir de 2024, le groupe a affecté plus de 500 à 700 organisations à l'échelle mondiale depuis son apparition au début de 2022. |
|
Violation du réseau municipal d'Austin, Texas (2020) |
En octobre 2020, la ville d'Austin a réalisé que des pirates parrainés par l'État russe (le groupe « Berserk Bear », selon les rapports) avaient complètement compromis l'infrastructure sans fil de la ville, et que les attaquants avaient maintenu l'accès aux systèmes internes pendant des mois avant d'être détectés. Selon les rapports du Microsoft Threat Intelligence Center, les attaquants ont utilisé des exploits, y compris Zerologon (CVE-2020-1472), pour pénétrer le réseau. Les responsables de la ville ont rapporté que les systèmes critiques n'ont pas été affectés et qu'aucune donnée personnelle n'a été perdue. En réponse, des agences fédérales et étatiques, y compris CISA et le FBI, ont émis des alertes et exhorté d'autres municipalités à réviser leur sécurité et à vérifier les signes de compromission. |
Conséquences des attaques Zerologon
Une attaque Zerologon peut semer le chaos dans une organisation. Une fois que les attaquants obtiennent l'accès Domain Admin, les dégâts peuvent épuiser les ressources financières et ternir la réputation de l'entreprise.
Domaine d'impact | Description |
|---|---|
|
Financier |
Les coûts directs comprennent les paiements de rançon, les enquêtes judiciaires, les services informatiques d'urgence, les dépenses de réponse et de récupération, et les frais réglementaires. Les coûts indirects peuvent inclure une perte de revenus due à des temps d'arrêt, des primes d'assurance cybernétique plus élevées et des investissements à long terme dans une nouvelle infrastructure de sécurité. Les sociétés cotées en bourse peuvent également subir une baisse de la valeur de leurs actions et une augmentation du coût du capital. |
|
Opérationnel |
Un DC compromis peut entraîner l'arrêt des services d'authentification dans toute l'organisation, tels que les connexions pour les e-mails, les partages de fichiers, les ERP et les applications cloud. Cela peut provoquer des pannes à l'échelle du domaine, l'arrêt des opérations commerciales et un temps d'arrêt prolongé pour les systèmes critiques. Lorsque les employés ne peuvent pas accéder aux systèmes critiques, les chaînes de production peuvent s'arrêter et les services clients (tels que le commerce électronique ou les portails patients) peuvent être hors ligne pendant des jours ou des semaines. |
|
Réputationnel |
Les clients, partenaires et investisseurs perdent confiance lorsque la sécurité fondamentale d'une entreprise échoue. La couverture médiatique négative, les réactions sur les réseaux sociaux et les déclassements par les analystes peuvent continuer même après la restauration des systèmes, rendant plus difficile la conquête de nouveaux clients ou le maintien des clients existants. |
|
Juridique/Réglementaire |
Les violations qui exposent des données personnelles ou réglementées (dossiers médicaux, données financières, archives gouvernementales) peuvent déclencher des notifications de violation obligatoires et des amendes en vertu du GDPR, HIPAA ou CCPA. Les organisations peuvent également faire face à des poursuites judiciaires, des actions en justice des actionnaires et à l'examen des organismes de réglementation. |
Cibles courantes des attaques Zerologon : Qui est à risque ?
Zerologon peut menacer toute organisation utilisant Active Directory, mais certains environnements sont plus vulnérables que d'autres, ou ont tendance à être plus tentants pour les attaquants.
|
Grandes entreprises |
Les grandes entreprises disposant de vastes forêts AD et de nombreux contrôleurs de domaine doivent souvent gérer des processus de patching et de gestion des changements complexes. Cela facilite la tâche des attaquants pour trouver un DC non patché et se déplacer latéralement à travers le réseau. |
|
Agences gouvernementales |
Les institutions du secteur public dépendent souvent de systèmes hérités et peuvent avoir des cycles de déploiement de correctifs plus lents. Les attaquants comptent sur ces retards pour exploiter les failles connues avant que les mises à jour ne soient appliquées. |
|
Fournisseurs d'infrastructures critiques |
Les secteurs tels que l'énergie, la santé et les transports sont des cibles de grande valeur car même une courte interruption peut avoir d'importantes conséquences socio-économiques et sur la sécurité publique. Plus la perturbation est grande, plus la probabilité d'un paiement de rançon est élevée. |
|
Établissements d'enseignement |
Les universités et les districts scolaires gèrent d'énormes bases d'utilisateurs diversifiées, des environnements de dispositifs mixtes avec des points de terminaison non gérés et des ressources limitées en cybersécurité. Cela crée une large surface d'attaque difficile à surveiller en continu. |
|
Gouvernements municipaux et locaux |
Ces entités fonctionnent avec une sécurité informatique limitée et une technologie obsolète. Des incidents tels que la violation du réseau municipal d'Austin, au Texas, montrent à quelle vitesse les attaquants peuvent exploiter ces lacunes pour perturber les services essentiels. |
|
Environnements multiplateformes |
Les organisations qui connectent des appareils Linux, macOS ou IoT à Active Directory peuvent laisser des failles de sécurité. Si les systèmes non-Windows ne sont pas entièrement mis à jour ou surveillés, les attaquants peuvent contourner les contrôles de sécurité. |
Évaluation des risques
Zerologon est un danger sérieux qui obtient la note de risque la plus élevée sur toute la ligne. La vulnérabilité permet aux attaquants de prendre le contrôle de l'environnement AD entier d'une organisation avec une relative facilité une fois qu'ils ont accès au réseau.
Microsoft et les principaux cadres de sécurité classent Zerologon (CVE-2020-1472) au sommet de leurs échelles de gravité. Cela signifie qu'ils considèrent Zerologon comme une vulnérabilité urgente et à fort impact qui nécessite une attention immédiate.
- Microsoft Security Advisory – L'a classé comme Critique, qui est la note de sévérité la plus élevée de Microsoft.
- Score CVSS v3.1 – Un score de 10.0 (Critique), le score maximal possible, reflétant sa facilité d'exploitation et le potentiel de prise de contrôle complète du domaine.
- CISA / Gouvernement des États-Unis – A ajouté CVE-2020-1472 au catalogue des vulnérabilités exploitées connues (KEV) et a émis plusieurs directives d'urgence exhortant à appliquer immédiatement des correctifs.
Prenons également en compte d'autres facteurs de risque :
Facteur de risque | Niveau |
|---|---|
|
Dommages potentiels |
Extrêmement élevé Une exploitation réussie donne un contrôle total du contrôleur de domaine, permettant une compromission complète du domaine, un vol de données à grande échelle et un déploiement rapide de rançongiciels. |
|
Facilité d'exécution |
Élevé Après avoir obtenu l'accès au réseau au DC, les attaquants nécessitent des compétences techniques minimales, car ils peuvent exploiter Zerologon avec des scripts de preuve de concept (PoC) disponibles publiquement. |
|
Probabilité |
Élevé La vulnérabilité a été activement exploitée par des groupes de rançongiciels et des acteurs APT dans le monde entier. |
Comment prévenir une attaque Zerologon
Pour prévenir une attaque Zerologon, les organisations devraient avoir besoin d'un mélange de correctifs opportuns, de contrôles d'authentification renforcés et de surveillance active.
Appliquez le correctif immédiatement
Installez sans tarder les mises à jour de sécurité d'août 2020 et de février 2021 de Microsoft sur chaque contrôleur de domaine. Ces correctifs ferment la faille cryptographique Netlogon et appliquent des protections de canal sécurisé qui bloquent l'exploit Zerologon.
Appliquez Secure RPC
Appliquez des connexions RPC (Remote Procedure Call) sécurisées en activant la clé de registre FullSecureChannelProtection et les paramètres de stratégie de groupe correspondants. Cela oblige tout le trafic Netlogon à utiliser des canaux cryptés et signés. Cette mesure empêche les attaquants de réduire la sécurité des connexions Netlogon, rendant ainsi difficile pour eux de manipuler ou d'usurper les communications légitimes des contrôleurs de domaine.
Restreindre les appareils non Windows
Segmentez ou contrôlez strictement les appareils Linux, macOS et IoT qui s'authentifient auprès d'Active Directory, en particulier ceux qui tentent de se connecter avec des privilèges élevés ou utilisent des méthodes d'authentification moins sécurisées. Des terminaux non-Windows non patchés ou mal configurés peuvent compromettre les contrôles de sécurité.
Mettez en œuvre MFA
Appliquez l'authentification multifacteur, en particulier pour tous les comptes privilégiés et de service. Bien que Zerologon contourne lui-même l'authentification, l'authentification multifacteur agit comme une défense essentielle après un compromis initial ou pour d'autres types d'attaques où les identifiants pourraient être volés. Une vérification supplémentaire réduit considérablement la chance que des identifiants volés seuls puissent permettre un mouvement latéral ou une élévation de privilèges.
Surveillez les activités suspectes
Suivez l'ID d'événement 4742 (modifications de compte d'ordinateur) et les événements de connexion Netlogon 5827–5831, qui peuvent révéler des échecs d'authentification répétés ou des réinitialisations de mot de passe inattendues — tous sont des signes précurseurs d'une tentative d'exploitation. En surveillant activement ces événements de sécurité pertinents et d'autres, les organisations peuvent rapidement identifier des activités suspectes, détecter des tentatives d'exploitation et initier une réponse à l'incident pour limiter les dégâts.
Solutions Netwrix - Comment Netwrix peut aider
Pour prévenir les attaques Zerologon, les produits de Netwrix tels que Netwrix Auditor peuvent être déterminants. Auditor permet aux organisations de surveiller en continu les modifications apportées aux paramètres et configurations critiques au sein d'Active Directory, de détecter les comportements anormaux et d'alerter les administrateurs en cas de modifications non autorisées ou d'activités suspectes. En suivant les écarts par rapport aux configurations de base et en fournissant une visibilité en temps réel, Netwrix Auditor aide les organisations à détecter rapidement et à contenir les tentatives d'escalade de privilèges telles que celles permises par Zerologon.
- Surveillance en temps réel : Netwrix Auditor surveille en continu les modifications apportées à Active Directory, y compris les configurations des contrôleurs de domaine, l'appartenance aux groupes de sécurité et les paramètres de stratégie de groupe. Il peut envoyer des alertes en temps réel aux administrateurs en cas de modification non autorisée ou lorsque des paramètres critiques sont modifiés. De cette manière, les administrateurs peuvent rapidement enquêter sur tout changement qui pourrait indiquer une attaque.
- Détection d'anomalies : L'engin de User Behavior and Anomaly Detection (UBAD) de Auditor utilise l'apprentissage automatique pour signaler des comportements de compte inhabituels, tels que des escalades de privilèges soudaines, des échecs de connexion répétés ou des réinitialisations de mot de passe inattendues, qui pourraient indiquer une exploitation de type Zerologon.
- Rapports de conformité : Netwrix Auditor offre des rapports de conformité prêts à l'emploi pour des cadres réglementaires tels que HIPAA, PCI DSS et GDPR. Ces rapports détaillés aident à vérifier que les politiques de sécurité (telles que la mise à jour opportune, la gestion des comptes privilégiés et les modifications du contrôle d'accès) sont strictement suivies pour détecter et prévenir les accès non autorisés.
Stratégies de détection, d'atténuation et de réponse
Pour protéger votre organisation contre une attaque Zerologon, vous avez besoin d'une approche multicouche : détection précoce des tentatives d'authentification suspectes, application rapide des correctifs et renforcement des contrôleurs de domaine, ainsi qu'un plan de réponse aux incidents en cas de compromission.
Détection
Pour la détection d'attaques Zerologon, vous devriez surveiller des signes spécifiques d'exploitation plutôt que de simples anomalies génériques.
- Journaux de débogage Netlogon : Surveillez les échecs rapides de NetrServerAuthenticate immédiatement suivis d'un succès provenant de la même adresse IP.
- Analyse de capture de paquets : Inspectez les traces réseau pour les tentatives d'authentification Netlogon qui utilisent des informations d'identification client tout-zéro (00:00:00:00:00:00:00:00) renvoyant STATUS_SUCCESS.
- Analyse de hachage : Recherchez le hachage NTLM bien connu 31d6cfe0d16ae931b73c59d7e0c089c0 dans l'historique des comptes du contrôleur de domaine, ce qui indique un mot de passe vide sur le compte du contrôleur de domaine.
- Surveillance des journaux d'événements : L'ID d'événement de sécurité Windows 4742 est l'entrée du journal qui enregistre « Un compte d'ordinateur a été modifié » dans Active Directory. Lorsque vous voyez cet événement avec le Type de connexion : Anonyme (ou « Connexion anonyme » comme l'appelant), cela signifie que quelqu'un sans identifiants valides a réussi à modifier un objet de compte d'ordinateur, indiquant qu'une exploitation de Zerologon a potentiellement eu lieu.
Atténuation
Les organisations peuvent atténuer le risque Zerologon en suivant certaines pratiques, telles que :
- Mettez à jour rapidement : Appliquez les mises à jour d'août 2020 et de février 2021 de Microsoft pour CVE-2020-1472 à chaque contrôleur de domaine.
- Appliquez Secure RPC : Activez la politique/paramètre de registre FullSecureChannelProtection et éliminez toutes les exceptions de politique. Cela force tout le trafic Netlogon entre les membres du domaine et les contrôleurs de domaine à utiliser RPC sécurisé avec une authentification cryptographique forte, bloquant l'astuce des identifiants tout-zéro utilisée dans l'exploit Zerologon.
- Réduire la surface d'attaque : Désactivez ou supprimez les comptes de machines non-Windows inutilisés dans Active Directory, appliquez le principe du moindre privilège aux appartenances de groupes et désactivez les protocoles obsolètes tels que SMBv1 et NTLMv1.
- Renforcez les contrôles d'Identity Management : Exigez l'authentification multi-facteurs (MFA) pour tous les comptes privilégiés afin de limiter l'impact en cas de vol d'identifiants.
- Surveillance avancée : Déployez des solutions EDR et SIEM pour détecter en temps réel les modèles d'authentification anormaux.
Réponse
Si vous soupçonnez ou confirmez une violation Zerologon, agissez rapidement et méthodiquement :
- Isoler le DC affecté: Déconnectez le contrôleur de domaine compromis du réseau pour arrêter l'activité de l'attaquant. Cela inclut le débranchement des câbles réseau physiques, le blocage de tout le trafic réseau vers et depuis le DC, et la désactivation des interfaces réseau.
- Réinitialiser les identifiants : Changez le mot de passe du compte machine du DC en une valeur longue et aléatoire.
- Reconstruire la confiance : Rétablissez les relations de confiance pour toutes les machines et comptes de service affectés. Vous pouvez utiliser l'outil en ligne de commande Netdom pour réinitialiser le canal sécurisé pour chaque client et serveur, ou utiliser des scripts PowerShell pour automatiser le processus.
- Rotation des Secrets Privileged Access Management : Réinitialisez tous les identifiants administratifs, y compris le compte KRBTGT, pour invalider les hachages volés et les tickets Kerberos. Le compte KRBTGT est la "clé maîtresse" de Kerberos dans un domaine. Un attaquant en possession de son hachage peut créer des "golden tickets" pour se faire passer pour n'importe quel utilisateur. En tant que meilleure pratique, réinitialisez le mot de passe de ce compte deux fois (avec un cycle complet d'expiration de ticket Kerberos entre les deux).
Réalisez une analyse forensique complète : Menez une enquête approfondie pour découvrir les mécanismes de persistance, les mouvements latéraux et tout autre actif compromis. Recherchez des éléments tels que des événements de connexion inhabituels, de nouveaux comptes administratifs, des modifications d'appartenance à des groupes et des processus suspects lors de l'analyse forensique.
Impact spécifique à l'industrie
Alors que la vulnérabilité Zerologon menace toute organisation utilisant Active Directory, ses conséquences peuvent varier selon le secteur. Voici des exemples de la manière dont elle peut affecter les industries critiques.
Industrie | Impact |
|---|---|
|
Santé |
Le secteur de la santé est une cible attrayante pour les attaquants. Avec une attaque ZeroLogon, les acteurs malveillants peuvent voler des données sensibles sur les patients, y compris les dossiers de santé électroniques (EHRs). Cela compromet non seulement la confidentialité des patients mais peut également entraîner des violations de la HIPAA, qui comportent de lourdes sanctions. Une violation entraîne presque certainement un temps d'arrêt qui retarde les soins aux patients ou perturbe les dispositifs médicaux dépendant de l'authentification Active Directory. Et si l'attaquant chiffre des systèmes critiques, cela peut gravement perturber les opérations hospitalières, la fonctionnalité des dispositifs médicaux et l'accès aux informations des patients, ce qui peut nuire aux soins des patients. |
|
Finance |
Dans le secteur financier, les conséquences d'une attaque ZeroLogon peuvent être dévastatrices. En compromettant un contrôleur de domaine, les attaquants peuvent accéder aux identifiants de multiples systèmes, allant des bases de données financières aux plateformes de trading. Cela peut entraîner des transactions frauduleuses, l'exfiltration de données, l'accès non autorisé aux données financières des clients et la manipulation des enregistrements financiers. Les institutions financières peuvent également faire face à de lourdes pénalités réglementaires en vertu du PCI DSS et du SOX, suivies d'une perte de confiance de la part des clients. |
|
Commerce de détail |
Dans le secteur du commerce de détail, les attaquants peuvent compromettre les systèmes de Point de Vente (POS), volant les données de cartes de crédit et d'autres informations clients. De plus, ils peuvent déployer des rançongiciels sur les réseaux de la chaîne d'approvisionnement, paralysant la logistique et la gestion des stocks. Cela pourrait conduire à un arrêt complet des opérations commerciales, à des pertes financières importantes, à des responsabilités juridiques et à des dommages à la réputation de la marque. |
Évolution des attaques & tendances futures
Les cybercriminels deviennent plus astucieux avec Zerologon. Ils automatisent les attaques, utilisent des outils d'IA pour repérer rapidement les contrôleurs de domaine non patchés et se concentrent sur les anciens systèmes qui ne peuvent pas être mis à jour. Cela signifie que l'écart entre la découverte et la compromission se réduit, donc l'application rapide de correctifs, la surveillance constante et des contrôles de réseau stricts sont essentiels.
Automatisation accrue
Les attaquants intègrent désormais des exploits Zerologon directement dans des kits d'outils de rançongiciels automatisés et des playbooks, leur permettant de prendre le contrôle d'un domaine en quelques minutes. Cette automatisation signifie qu'ils peuvent scanner, s'introduire et se déplacer à travers le réseau beaucoup plus rapidement et avec moins de compétences techniques qu'auparavant. Dans de nombreux cas, ils frappent avant même que les équipes de sécurité ne s'en aperçoivent.
Conseil pour les défenseurs : Concentrez-vous sur la détection rapide (journaux Netlogon, captures de paquets) et automatisez la gestion des correctifs, afin que la remédiation puisse suivre le rythme des attaques automatisées.
Intégration avec la Reconnaissance pilotée par l'IA
Les attaquants commencent à associer le balayage automatique à l'IA pour trouver plus rapidement les contrôleurs de domaine vulnérables. Leurs outils peuvent détecter des indices dans le réseau, prédire quels serveurs ne sont pas patchés ou utilisent des protocoles obsolètes, et sélectionner les contrôleurs de domaine à plus haute valeur. L'IA les aide même à choisir le bon moment et le chemin d'attaque, en fonction du comportement observé du réseau, rendant les attaques plus précises et plus difficiles à prévoir.
Conseil pour les défenseurs : Améliorez l'hygiène et la surveillance du réseau. Alimentez EDR et SIEM avec un contexte plus riche afin que vos propres analyses puissent détecter et bloquer ces menaces.
Ciblage continu des systèmes hérités
Les systèmes obsolètes et isolés qui ne reçoivent plus de mises à jour des fournisseurs restent une cible privilégiée. Les attaquants recherchent des environnements où des exceptions ou des listes d'autorisation existent pour la compatibilité avec les versions antérieures (par exemple, des systèmes qui dépendent d'anciens comportements Netlogon ou de versions de systèmes d'exploitation non prises en charge). Une fois que les attaquants pénètrent ces machines, ils peuvent les utiliser comme points d'ancrage à long terme pour des attaques répétées.
Conseil pour les défenseurs : Si vous ne pouvez pas patcher ces systèmes, isolez-les du reste du réseau, appliquez des contrôles compensatoires (segmentation du réseau, règles strictes de pare-feu et serveurs intermédiaires), supprimez les protocoles inutiles et marquez-les comme à haut risque pour une surveillance stricte.
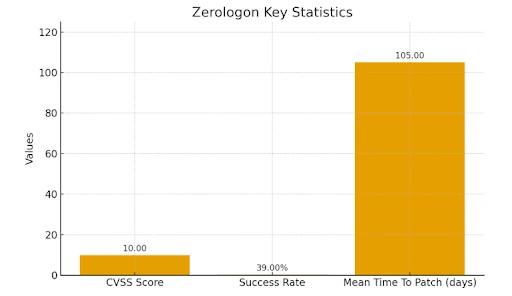
Statistiques clés & Infographies
La vulnérabilité Zerologon (CVE-2020-1472) est rapidement devenue l'une des menaces Windows les plus discutées car elle est facile à exploiter et peut causer d'énormes dommages. Ces chiffres montrent à quel point il est crucial de corriger rapidement et de rester en avance avec des défenses proactives solides.
- Score CVSSLa vulnérabilité a reçu le score de base CVSS maximum de 10.0, reflétant sa facilité d'exploitation, la capacité à obtenir des privilèges d'administrateur de domaine sans identifiants, et le potentiel de compromission complète du domaine.
- Taux de réussite de l'exploitationLes chercheurs ont découvert que une seule tentative de Zerologon a environ 0,39 % de chances de réussir, ce qui signifie qu'un attaquant a généralement besoin d'environ 256 essais pour réinitialiser le mot de passe machine d'un contrôleur de domaine. Comme ces tentatives peuvent être scriptées, la compromission peut survenir en moins d'une minute.
- Retard dans l'adoption des correctifsMalgré la publication de correctifs par Microsoft en août 2020 et de nouveau en février 2021, les études du secteur révèlent que le temps moyen pour appliquer les correctifs (MTTP) pour les vulnérabilités critiques de Windows est de 60 à 150 jours après leur sortie. Ce retard offre aux attaquants une large fenêtre pour exploiter les systèmes non patchés.
Voici un diagramme à barres mettant en évidence ces statistiques.
Réflexions finales
La vulnérabilité Zerologon a été découverte pour la première fois en 2020 par le chercheur en sécurité Tom Tervoort de Secura. Microsoft a publié un correctif critique le 11 août 2020 dans le cadre de ses mises à jour mensuelles du Patch Tuesday. Une fois le correctif disponible, Secura a publié un rapport technique détaillé avec zerologon expliqué en septembre 2020, ce qui a attiré davantage l'attention sur la faille et encouragé d'autres à construire des exploits de preuve de concept publics.
Zerologon est un rappel qu'une seule faille négligée peut mettre en danger tout un domaine Windows. Sa facilité d'exécution, son impact critique et l'adoption lente des correctifs ont contribué à sa popularité, tout en soulignant la nécessité d'appliquer les correctifs en temps opportun, de surveiller en continu, de disposer de contrôles d'identité solides et de plans de réponse aux incidents testés.
FAQ
Partager sur
Voir les attaques de cybersécurité associées
Abus des autorisations d'application Entra ID – Fonctionnement et stratégies de défense
Modification de AdminSDHolder – Fonctionnement et stratégies de défense
Attaque AS-REP Roasting - Fonctionnement et stratégies de défense
Attaque Hafnium - Fonctionnement et stratégies de défense
Attaques DCSync expliquées : Menace pour la sécurité d'Active Directory
Attaque Golden SAML
Comprendre les attaques Golden Ticket
Attaque des comptes de service gérés par groupe
Attaque DCShadow – Fonctionnement, exemples concrets et stratégies de défense
Injection de prompt ChatGPT : Comprendre les risques, exemples et prévention
Attaque d'extraction de mot de passe NTDS.dit
Attaque Pass the Hash
Explication de l'attaque Pass-the-Ticket : Risques, Exemples et Stratégies de Défense
Attaque par pulvérisation de mots de passe
Attaque d'extraction de mot de passe en clair
Attaque Kerberoasting – Fonctionnement et stratégies de défense
Attaques de rançongiciels sur Active Directory
Déverrouillage d'Active Directory avec l'attaque Skeleton Key
Mouvement latéral : Qu'est-ce que c'est, comment ça fonctionne et préventions
Attaques de l'homme du milieu (MITM) : ce qu'elles sont et comment les prévenir
Pourquoi PowerShell est-il si populaire auprès des attaquants ?
4 attaques de compte de service et comment s'en protéger
Comment prévenir les attaques de logiciels malveillants d'affecter votre entreprise
Qu'est-ce que le Credential Stuffing ?
Compromettre SQL Server avec PowerUpSQL
Qu'est-ce que les attaques de Mousejacking et comment se défendre contre elles
Vol de credentials avec un fournisseur de support de sécurité (SSP)
Attaques par tables arc-en-ciel : leur fonctionnement et comment se défendre
Un regard approfondi sur les attaques par mot de passe et comment les arrêter
Reconnaissance LDAP
Contournement de l'authentification multifacteur avec l'attaque Pass-the-Cookie
Attaque Silver Ticket
