Diebstahl von Anmeldeinformationen mit einem Security Support Provider (SSP)
Mimikatz provides attackers with several different ways to steal credentials from memory or extract them from Active Directory. One of the most interesting options is the MemSSP command. An adversary can use this command to register a malicious Security Support Provider (SSP) on a Windows member server or domain controller (DC) — and that SSP will log all passwords in clear text for any users who log on locally to that system.
Ausgewählte verwandte Inhalte:
In diesem Beitrag werden wir diesen Angriff untersuchen und wie Angreifer ihn nutzen können, um ihre Privilegien zu erhöhen.
SSP-Angriffsszenarien
Ein Security Support Provider ist eine dynamische Linkbibliothek (DLL), die an sicherheitsbezogenen Operationen beteiligt ist, einschließlich Authentifizierung. Microsoft bietet eine Reihe von SSPs an, darunter Pakete für Kerberos und NTLM. Lassen Sie uns einige der Gründe betrachten, warum ein Angreifer möglicherweise eine bösartige SSP auf einem Computer registrieren möchte:
- Ein Angreifer hat als lokaler Administrator einen Mitgliedsserver kompromittiert, hat jedoch eingeschränkte Rechte, sich seitlich durch die Domäne zu bewegen.
- Ein Angreifer hat als Domain Admin oder Administrator einen DC kompromittiert, möchte aber seine Privilegien auf Enterprise Admin erhöhen, um sich seitlich über Domänen hinwegzubewegen.
- Ein Angreifer hat als Domain-Admin mithilfe eines Pass-the-Hash-Angriffs einen DC kompromittiert, möchte jedoch das Klartextpasswort des Admins nutzen, um sich bei anderen Anwendungen wie Outlook Web Access oder einer Remote-Desktop-Verbindung anzumelden.
In jedem dieser Szenarien kann ein SSP-Angriff sehr effektiv sein.
Durchführung eines SSP-Angriffs
Die Durchführung eines SSP-Angriffs ist sehr einfach. Für diesen Beitrag konzentrieren wir uns auf die Angriffe, die einen Domain-Controller zum Ziel haben. Nehmen wir an, wir haben ein Domain Admin-Konto kompromittiert und möchten einen bösartigen SSP im Speicher injizieren. Alles, was wir tun müssen, ist den Befehl misc::memssp in Mimikatz: auszuführen.
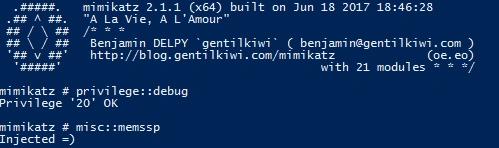
Nun wird das SSP im Speicher injiziert. Wenn jedoch der DC neu gestartet wird, geht das SSP verloren und muss erneut injiziert werden. Dies kann gelöst werden, indem man eine DLL als SSP registriert, die mit Mimikatz geliefert wird.
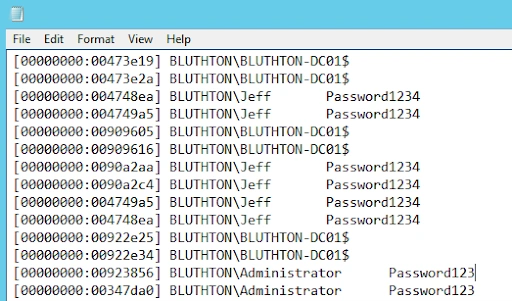
Sobald der SSP registriert ist, werden alle Benutzer, die sich am DC anmelden, sowie alle lokalen Dienste, ihre Passwörter in der Datei c:WindowsSystem32mimilsa.log protokollieren. Diese Datei wird die Klartext-Passwörter für alle Benutzer enthalten, die sich angemeldet haben und Dienstkonten, die auf dem System laufen:
Schutz vor SSP-Angriffen
Detection
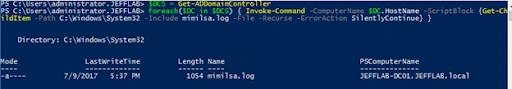
SSP-Angriffe können schwer zu erkennen sein. Um zu überprüfen, ob einige Ihrer DCs bereits kompromittiert wurden, können Sie den folgenden PowerShell-Befehl ausführen, um jeden DC in der Domäne auf das Vorhandensein der mimilsa.log-Datei zu überprüfen. Hoffentlich sind die Ergebnisse leer.
Prävention
Da SSP-Angriffe auf DCs voraussetzen, dass ein Angreifer den DC als Domain Admin oder Administrator kompromittiert hat, besteht die beste Prävention darin, diese Konten vor Kompromittierung zu schützen, indem die Mitgliedschaft in diesen Gruppen streng begrenzt, eine starke Kontenverwaltung durchgesetzt und die Aktivitäten von privilegierten Konten überwacht werden.
Wie Netwrix helfen kann
Erkennen Sie Sicherheitsprobleme in Ihrer AD-Umgebung und beheben Sie die Lücken, bevor Angreifer sie mit Tools wie Mimikatz ausnutzen können, mit der Netwrix Active Directory security solution. Sie ermöglicht es Ihnen:
- Decken Sie Sicherheitsrisiken in Active Directory auf und priorisieren Sie Ihre Minderungsmaßnahmen.
- Verstärken Sie die Sicherheitskonfigurationen in Ihrer IT-Infrastruktur.
- Erkennen und enthalten Sie umgehend auch fortgeschrittene Bedrohungen wie Golden Ticket-Angriffe.
- Reagieren Sie sofort auf bekannte Bedrohungen mit automatisierten Antwortoptionen.
- Minimieren Sie Geschäftsunterbrechungen mit schneller Active Directory-Wiederherstellung.
Teilen auf
Zugehörige Cybersecurity-Angriffe anzeigen
Missbrauch von Entra ID-Anwendungsberechtigungen – Funktionsweise und Verteidigungsstrategien
AdminSDHolder-Modifikation – Funktionsweise und Verteidigungsstrategien
AS-REP Roasting Attack - Funktionsweise und Verteidigungsstrategien
Hafnium-Angriff - Funktionsweise und Verteidigungsstrategien
DCSync-Angriffe erklärt: Bedrohung für die Active Directory Security
Pass-the-Hash-Angriff
Verständnis von Golden Ticket-Angriffen
Angriffe auf Group Managed Service Accounts
DCShadow-Angriff – Funktionsweise, Beispiele aus der Praxis & Verteidigungsstrategien
ChatGPT Prompt Injection: Risiken, Beispiele und Prävention verstehen
NTDS.dit-Passwortextraktionsangriff
Kerberoasting-Angriff – Funktionsweise und Verteidigungsstrategien
Pass-the-Ticket-Attacke erklärt: Risiken, Beispiele & Verteidigungsstrategien
Password-Spraying-Angriff
Angriff zur Extraktion von Klartext-Passwörtern
Zerologon-Schwachstelle erklärt: Risiken, Exploits und Milderung
Ransomware-Angriffe auf Active Directory
Active Directory mit dem Skeleton Key-Angriff entsperren
Laterale Bewegungen: Was es ist, wie es funktioniert und Präventionsmaßnahmen
Man-in-the-Middle (MITM)-Angriffe: Was sie sind & Wie man sie verhindert
Silver Ticket Attack
4 Angriffe auf Dienstkonten und wie man sich dagegen schützt
Warum ist PowerShell so beliebt bei Angreifern?
Wie Sie Malware-Angriffe daran hindern, Ihr Geschäft zu beeinträchtigen
Kompromittierung von SQL Server mit PowerUpSQL
Was sind Mousejacking-Angriffe und wie kann man sich dagegen verteidigen
Was ist Credential Stuffing?
Rainbow-Table-Attacken: Wie sie funktionieren und wie man sich dagegen verteidigt
Ein umfassender Blick auf Passwortangriffe und wie man sie stoppt
LDAP-Aufklärung
Umgehen der MFA mit dem Pass-the-Cookie-Angriff
Golden SAML-Angriff
