Reconocimiento LDAP
El reconocimiento es una parte importante de cualquier ataque exitoso. Hay dos formas clave: el reconocimiento inicial o externo que se realiza antes de que un adversario se infiltre en una organización, y el reconocimiento interno donde descubren información y contexto adicionales sobre el entorno de la organización.
El reconocimiento LDAP es una técnica de reconocimiento interno que los atacantes utilizan para descubrir usuarios, grupos y computadoras en Active Directory. Utilizan consultas LDAP para aumentar su conocimiento del entorno, lo que puede ayudarles a encontrar objetivos y planificar las siguientes etapas de su ataque. Debido a que esta técnica es utilizada por adversarios que ya han infiltrado una organización, es una técnica de reconocimiento interno (en lugar de externo).
Resumen de amenazas
Objetivo: Active Directory
Herramientas: BloodHound, PowerSploit, SharpHound, Spray
Táctica ATT&CK®: Descubrimiento
Técnica ATT&CK: T1087.002
Dificultad
Detección: Difícil
Mitigación: Difícil
Respuesta: Media
Realizando reconocimiento utilizando LDAP
PASO 1: Obtener un punto de apoyo
Los adversarios utilizan una variedad de técnicas para obtener un punto de apoyo en el entorno de TI de una organización, incluyendo ataques de phishing, watering hole y de rociado de contraseñas. Aquí está cómo un adversario que ha obtenido una lista de posibles nombres de usuario puede llevar a cabo un ataque de rociado de contraseñas utilizando Spray, un script de bash creado para realizar ataques de rociado de contraseñas en múltiples plataformas, contra el servidor de red privada virtual (VPN) de la organización:
[attacker@machine ~]$ spray.sh -cisco vpn.org.com usernames.txt passwords.txt 1 35
Valid Credentials joed Summer2020
PASO 2: Realizar reconocimiento utilizando LDAP
El adversario utiliza las credenciales comprometidas para autenticarse en la VPN y obtener acceso a la red, y luego usa esas mismas credenciales para consultar Active Directory. Pueden enumerar Active Directory utilizando el módulo de PowerShell ActiveDirectory, o automatizar el descubrimiento con herramientas como BloodHound y PowerSploit. En este ejemplo, el adversario utiliza PowerShell para buscar posibles contraseñas en los atributos de descripción de los usuarios:
PS> Import-Module ActiveDirectory
PS> Get-ADObject -LDAPFilter "(&(objectClass=user)(description=*pass*))" -property * | Select-Object SAMAccountName, Description, DistinguishedName
SAMAccountName DescriptionDistinguishedName
-------------- ----------------------------
AlicePassword: P@ssw0rd123!CN=Alice,OU=Users,DC=domain,DC=com
PS>
PASO 3: Utilizar la información para avanzar en los objetivos
Utilizando las credenciales que han encontrado, el adversario lleva a cabo un reconocimiento interno adicional utilizando herramientas como BloodHound y SharpHound, que ayudan a desenredar complejas redes de permisos. Con esta información, el adversario puede trazar rutas hacia objetivos, como el dominio del dominio.
La gráfica a continuación ilustra un ejemplo. Supongamos que un atacante obtiene las credenciales de la cuenta de usuario Alice. Esa cuenta tiene permisos WriteDACL y WriteOwner sobre el usuario Eve, lo que significa que Alice puede otorgarse acceso a la cuenta de Eve. Eve tiene derechos para restablecer la contraseña de la cuenta Bob, y Bob tiene permisos (otorgados a través de la propagación de AdminSDHolder) para modificar el grupo de Administradores del Dominio. Por lo tanto, ¡encontrar la contraseña de Alice fue muy valioso para el adversario!
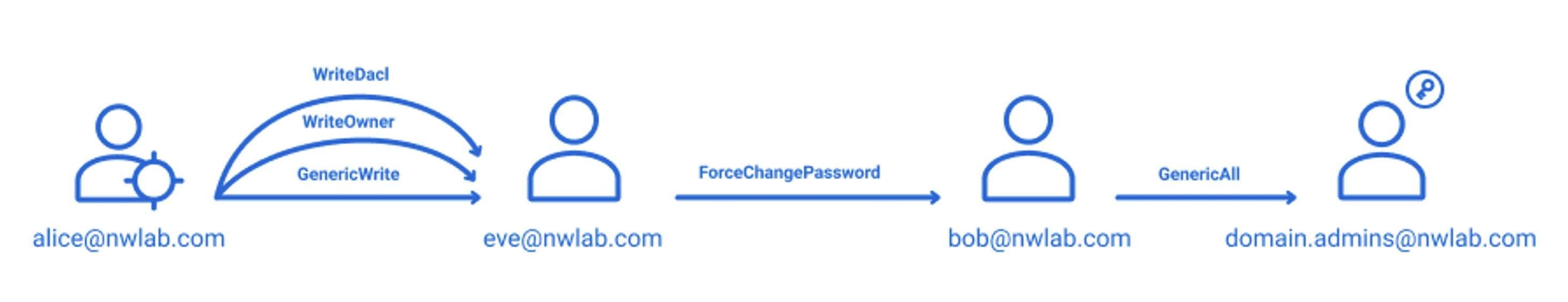
Resultado
Después de recolectar datos con SharpHound.exe -C All, el adversario puede cargar el conjunto de datos en BloodHound para explorar caminos hacia el dominio del dominio.
Detectar, Mitigar y Responder
Detectar
Dificultad: Difícil
El protocolo LDAP se utiliza con frecuencia en Active Directory, por lo que es difícil separar las consultas maliciosas de las legítimas. Además, Active Directory no proporciona un mecanismo para registrar las consultas exactas recibidas; sin embargo, se puede lograr cierto grado de perfilado y monitoreo del acceso a atributos específicos utilizando el evento 4662 en la subcategoría Audit Directory Service Access.
Monitorear el tráfico de red recibido por los controladores de dominio para consultas LDAP específicas puede ayudar a detectar actividad de adversarios. La siguiente tabla muestra una pequeña muestra de los tipos de consultas que deberían ser infrecuentes en una operación normal, pero que pueden proporcionar señales fuertes de actividad de adversarios:
Consulta | Información Recopilada |
|---|---|
|
(&(ObjectClass=user)(servicePrincipalName=*)) |
Todos los objetos de usuario que tienen un ServicePrincipalName configurado |
|
(userAccountControl:1.2.840.113556.1.4.803:=65536) |
Objetos que tienen establecido Password Never Expires |
|
(userAccountControl:1.2.840.113556.1.4.803:=4194304) |
Objetos que no requieren pre-autenticación Kerberos |
|
(sAMAccountType=805306369) |
Todos los objetos de computadora |
|
(sAMAccountType=805306368) |
Todos los objetos de usuario |
|
(userAccountControl:1.2.840.113556.1.4.803:=8192) |
Todos los objetos del controlador de dominio |
|
(primaryGroupID=512) |
Todos los administradores de dominio que usan PrimaryGroupID |
Mitigar
Dificultad: Difícil
Debido a que LDAP desempeña un papel esencial en las operaciones normales de Active Directory, las organizaciones no pueden simplemente bloquear su uso. En su lugar, concéntrese en mitigaciones que prevengan la infiltración desde el principio: conciencia y capacitación de usuarios, detección y respuesta ante compromisos de endpoints, detección y prevención de phishing, seguridad de correo electrónico, autenticación de múltiples factores (MFA) y así sucesivamente.
Responder
Dificultad: Media
Si se detecta reconocimiento LDAP en el entorno, active el proceso de respuesta ante incidentes y alerte al equipo de respuesta ante incidentes.
Si se confirma la presencia de un adversario:
- Restablezca la contraseña y deshabilite la cuenta de usuario que realiza reconocimiento.
- Ponga en cuarentena el ordenador fuente para la investigación forense y las actividades de erradicación y recuperación.
Compartir en
Ver ataques de ciberseguridad relacionados
Abuso de permisos de aplicaciones Entra ID – Cómo funciona y estrategias de defensa
Modificación de AdminSDHolder – Cómo funciona y estrategias de defensa
Ataque AS-REP Roasting - Cómo funciona y estrategias de defensa
Ataque Hafnium - Cómo funciona y estrategias de defensa
Ataques DCSync explicados: Amenaza a la seguridad de Active Directory
Ataque de Pass the Hash
Entendiendo los ataques de Golden Ticket
Ataque de Cuentas de Servicio Administradas por Grupo
Ataque DCShadow – Cómo funciona, ejemplos del mundo real y estrategias de defensa
ChatGPT Prompt Injection: Comprensión de riesgos, ejemplos y prevención
Ataque de extracción de contraseñas de NTDS.dit
Ataque de Kerberoasting – Cómo funciona y estrategias de defensa
Explicación del ataque Pass-the-Ticket: Riesgos, ejemplos y estrategias de defensa
Ataque de Password Spraying
Ataque de extracción de contraseñas en texto plano
Explicación de la vulnerabilidad Zerologon: Riesgos, Explotaciones y Mitigación
Ataques de ransomware a Active Directory
Desbloqueando Active Directory con el ataque Skeleton Key
Movimiento lateral: Qué es, cómo funciona y prevenciones
Ataques de Hombre en el Medio (MITM): Qué son y cómo prevenirlos
¿Por qué es PowerShell tan popular entre los atacantes?
¿Qué es Credential Stuffing?
Comprometiendo SQL Server con PowerUpSQL
¿Qué son los ataques de Mousejacking y cómo defenderse de ellos?
Robo de credenciales con un Proveedor de Soporte de Seguridad (SSP)
Ataques de Rainbow Table: Cómo funcionan y cómo defenderse de ellos
Una mirada exhaustiva a los ataques de contraseñas y cómo detenerlos
Ataque de Silver Ticket
Eludir MFA con el ataque Pass-the-Cookie
Ataque Golden SAML
