Movimiento lateral: Qué es, cómo funciona y prevenciones
El movimiento lateral en la ciberseguridad es una técnica para navegar a través de la red para obtener datos críticos desde una ubicación comprometida, es decir, credenciales robadas o un adjunto de correo infectado. Los atacantes logran silenciosamente objetivos como la extracción de datos, encriptar datos sensibles, dañar la infraestructura para obtener ganancias financieras y espionaje. Se emplean múltiples técnicas para reducir la superficie de ataque, como políticas estrictas de Identity and Access Management (IAM), revisión regular de privilegios, despliegue de sistemas de monitoreo de amenazas automatizados para remediar patrones de actividad de usuarios maliciosos de manera oportuna.
Atributo | Detalles |
|---|---|
|
Tipo de ataque |
Movimiento lateral |
|
Nivel de impacto |
Alto / Crítico |
|
Target |
Empresas, Gobiernos, Infraestructura Crítica |
|
Vector de Ataque Primario |
Red, Credenciales robadas, Vulnerabilidades explotadas |
|
Motivación |
Ganancia financiera (Ransomware), Espionaje, Robo de datos, Sabotaje del sistema |
|
Métodos comunes de prevención |
Zero Trust, MFA, Segmentación de Redes, Endpoint Detection & Response (EDR), SIEM, User Behavior Analytics (UBA) |
Factor de riesgo | Nivel |
|---|---|
|
Daño potencial |
Crítico |
|
Facilidad de ejecución |
De medio a alto |
|
Probabilidad |
Alto |
¿Qué es el movimiento lateral?
El Movimiento Lateral es el conjunto de técnicas utilizadas por los atacantes cibernéticos para obtener acceso inicial a una red y así poder navegar y propagarse en sub-sistemas, aplicaciones y datos para realizar actividades maliciosas. En lugar de atacar directamente el sistema objetivo, los atacantes se mueven lateralmente a través de la red, evaluando objetivos valiosos, escalando privilegios y posicionándose para un ataque mayor.
El propósito del movimiento lateral durante un ataque es expandir el control y alcance dentro de la red comprometida. Esta fase permite a los atacantes localizar y acceder a objetivos de alto valor como almacenes de datos sensibles, servidores críticos como controladores de dominio, escalar privilegios como obtener control administrativo, mantener acceso no detectado a largo plazo en la red y prepararse para el ataque final como extracción de datos, despliegue de ransomware o interrupción de servicios críticos.
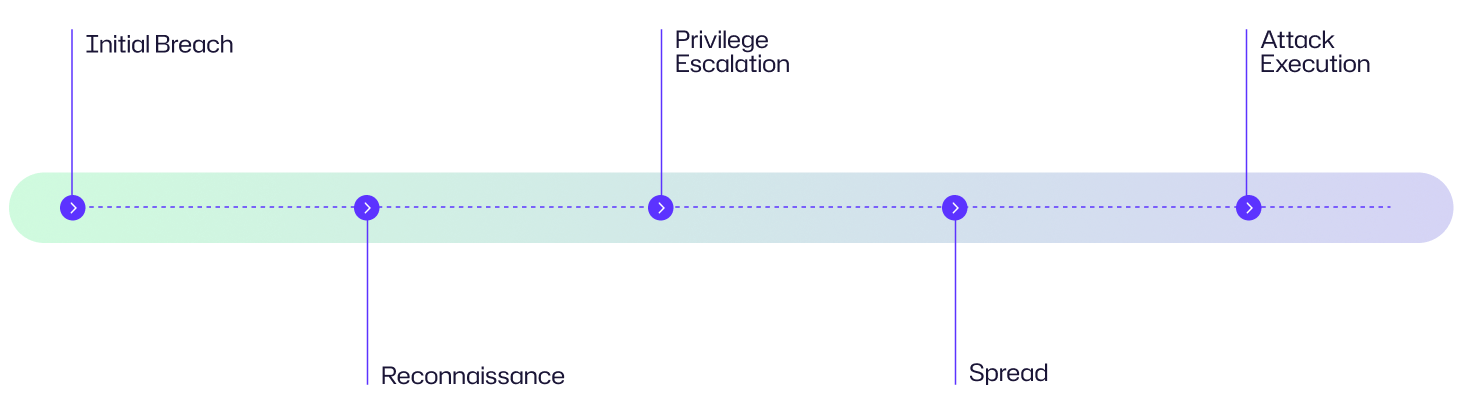
- Acceso inicial: Los atacantes obtienen acceso a la red mediante correos electrónicos de phishing, infecciones de malware o con credenciales robadas.
- Reconocimiento: una vez que los atacantes obtienen acceso, exploran la red para entender su estructura e intentan identificar activos como sistemas y cuentas de usuario débiles, servidores y aplicaciones.
- Escalación de Privilegios: después de la exploración inicial, los atacantes intentan obtener acceso de mayor nivel robando credenciales y explotando vulnerabilidades conocidas o de día cero de aplicaciones y sistemas.
- Movimiento Lateral: utilizando herramientas como el protocolo de escritorio remoto, PowerShell y otras utilidades administrativas, el atacante se desplaza de un sistema a otro, ampliando su control y alcance.
- Ataque Final: Después de mapear la red y obtener acceso suficiente en sub-sistemas, los atacantes ejecutan su ataque final robando datos sensibles, desplegando ransomware o destruyendo servicios o sistemas críticos.
¿Cómo funciona el movimiento lateral? (Desglose paso a paso)
El movimiento lateral es un proceso de múltiples fases utilizado por los atacantes después de que tienen éxito en su brecha inicial de la seguridad de la red para navegar y obtener control total o parcial de la red y sus subsistemas para lograr su objetivo malicioso. A continuación se ofrece un desglose más detallado de cada fase.
Acceso inicial
Existen diferentes técnicas utilizadas por los ciberdelincuentes para penetrar la defensa de la red y obtener acceso a al menos un sistema.
Correos electrónicos de phishing
Existen diferentes tipos de ataques de phishing utilizados para atrapar a las personas y hacer que revelen información sensible.
Spear phishing
Los correos electrónicos dirigidos están diseñados para engañar a individuos específicos con el fin de que revelen credenciales o hagan clic en enlaces y adjuntos maliciosos para infectar sistemas.
Whaling
Un tipo específico de ataque dirigido a individuos de alto perfil como CEOs o CFOs, para obtener acceso a sus cuentas privilegiadas.
Compromiso del Correo Electrónico Empresarial (BEC)
Los atacantes se hacen pasar por entidades de confianza, es decir, proveedores, socios comerciales, colegas a través de correo electrónico para revelar información sensible o realizar transferencias de fondos.
Infecciones por malware
El malware como los keyloggers, los Remote Access Trojans (RATs) se despliegan a través de adjuntos de correo electrónico, dispositivos USB infectados, anuncios de sitios legítimos con código ejecutable infectado para abrir una puerta trasera en la red objetivo.
Ataque de fuerza bruta
Herramientas automatizadas que prueban diferentes combinaciones de nombre de usuario y contraseña, se utilizan para atacar sistemáticamente servicios expuestos a Internet como el Protocolo de Escritorio Remoto (RDP), VPNs o aplicaciones web.
Vulnerabilidades de software
Los atacantes identifican y explotan vulnerabilidades conocidas en sistemas operativos, aplicaciones, servidores web o dispositivos de red que aún no han sido parcheados. Los exploits de Zero Day, para los cuales aún no hay un parche disponible, son altamente efectivos para obtener acceso no autorizado.
Reconocimiento Interno
Después del acceso inicial, los atacantes comienzan la siguiente fase de Reconocimiento interno, recopilando información silenciosamente sobre la red y sistemas conectados como el Mapeo de Red, identificando cuentas de usuario con privilegios elevados, localizando servidores críticos, carpetas compartidas, bases de datos y evaluando diferentes configuraciones de seguridad.
Las herramientas comunes utilizadas en este ejercicio son las siguientes
- Símbolo del sistema y PowerShell para ejecutar scripts en memoria y evaluar configuraciones del sistema y de la red.
- PSExec, una herramienta de línea de comandos utilizada para ejecutar comandos en sistemas remotos para evaluar la accesibilidad y los niveles de privilegios.
- NetStat, una utilidad de línea de comandos utilizada para recopilar información sobre conexiones de red, puertos en escucha y conexiones establecidas.
El enfoque de la fase de reconocimiento es identificar cuentas con privilegios administrativos como administradores de dominio, cuentas predeterminadas con contraseñas por defecto conocidas, localizar carpetas de sistema o compartidas, servidores de bases de datos o soluciones ERP con información sensible.
Credential Dumping & Privilege Escalation
Esta fase implica la extracción de credenciales, nombres de usuario y contraseñas de la memoria del sistema, registros o archivos con herramientas especialmente diseñadas como keyloggers y Mimikatz.
Los keyloggers capturan silenciosamente las pulsaciones de teclas y roban datos sensibles como el nombre de usuario y la contraseña o las respuestas a preguntas de seguridad para MFA. Mimikaz especialmente se utiliza para extraer contraseñas en texto plano, Hashes de Contraseñas, PINs y tickets de Kerberos y apunta a componentes de Windows como LSASS, WDigest y Kerberos.
Una vez que se adquieren las credenciales, se emplean diferentes técnicas para escalar privilegios, en sistemas locales o a nivel de dominio explotando políticas débiles y configuraciones erróneas. Los atacantes explotan vulnerabilidades conocidas del sistema operativo, servicios o tareas programadas con cuentas privilegiadas e impersonan el token de acceso de usuario de una cuenta privilegiada.
Movimiento lateral y propagación
Después de obtener credenciales privilegiadas, los atacantes expanden aún más el movimiento lateral para navegar por diferentes sistemas en la red con el fin de localizar repositorios de información sensible para su ataque final. Las técnicas incluyen.
Pass-the-Hash (PtH)
Pass-the-Hash (PtH) es una técnica astuta utilizada por atacantes para autenticarse en un sistema remoto sin necesidad de contraseñas en texto plano. Cuando cualquier usuario se autentica en un sistema Windows, su contraseña se convierte en un hash criptográfico y se utiliza para la verificación posterior. Los atacantes extraen estos hashes de contraseñas utilizando herramientas especiales para su actividad maliciosa y esta técnica es efectiva para eludir diferentes mecanismos de detección.
Pass-the-Ticket (PtT)
Pass-the-Ticket (PtT) se utiliza para máquinas unidas a un Dominio, cuando un usuario inicia sesión en una máquina unida a un Dominio con autenticación Kerberos se le asigna un Ticket para autenticación repetida sin volver a ingresar las credenciales. Ese ticket se utiliza en el ataque Pass-the-Ticket y se usa para acceder a diferentes recursos en la red suplantando al usuario sin conocer su contraseña.
Protocolo de Escritorio Remoto (RDP)
El protocolo de Escritorio Remoto (RDP) permite el acceso remoto a dispositivos y es un protocolo comúnmente utilizado. El secuestro de sesiones activas de servicios remotos debido a configuraciones erróneas de RDP o la reutilización de credenciales es una forma efectiva de movimiento lateral y proporciona una interfaz gráfica completa como si el atacante estuviera sentado frente a ese sistema.
Ejecución del Ataque Final
Después de la ejecución exitosa de las diferentes fases de movimiento lateral, los atacantes ejecutan sus objetivos como desplegar ransomware, extraer información sensible o sabotear infraestructura crítica.
Los ransomwares son malwares que cifran archivos en unidades locales o comparticiones de administrador en la red, haciendo que los datos sean inutilizables sin la clave de descifrado. Después del cifrado, los atacantes suelen dejar notas de rescate en el sistema afectado exigiendo un pago para liberar la clave de descifrado y en algunos ataques sofisticados, también se eliminan o cifran las copias de seguridad para impedir la restauración sin pago.
La exfiltración de datos sensibles es otro objetivo común de los atacantes para robar datos corporativos con fines de extorsión o para venderlos en mercados de la darknet. Después de lograr cierto acceso privilegiado e identificar las fuentes de datos en la red, los atacantes comienzan a enviar datos a sus servidores, almacenamiento en la nube o dispositivos de almacenamiento extraíbles y cubren sus rastros. Estos datos pueden ser registros financieros, datos privados de empleados o clientes y propiedad intelectual como código fuente o diseños de productos.
El sabotaje de la infraestructura crítica implica principalmente obtener el control de la tecnología operativa de las redes eléctricas, hospitales e instituciones gubernamentales para propagar la interrupción y la denegación de servicio. Una vez que se establece el Privileged Access en estas organizaciones objetivo, se despliegan malwares o se configura el equipo para daños permanentes de tal manera que la operación o servicio previsto de la organización se retrase o se cierre por completo.
Diagrama de flujo de ataque
Ejemplos de movimiento lateral
Caso | ¿Qué pasó |
|---|---|
|
Violación de SolarWinds (2020) |
Los atacantes explotaron la actualización del software Orion, moviéndose lateralmente para comprometer agencias gubernamentales de EE. UU. |
|
NotPetya (2017) |
Se utilizó el robo de credenciales y la propagación de exploits, paralizando negocios en todo el mundo. |
|
WannaCry (2017): |
Se propagó rápidamente utilizando el exploit EternalBlue, afectando a más de 200,000 sistemas. |
Case | Qué pasó |
|---|---|
|
Incidente de SolarWinds (2020) |
Los atacantes explotaron los mecanismos de actualización del software Orion para obtener acceso a la infraestructura de diferentes organizaciones, incluidas agencias del gobierno de EE. UU. Inicialmente, los atacantes comprometieron la configuración de construcción de software de SolarWind e insertaron código malicioso en las actualizaciones de Orion, como estaban firmadas digitalmente parecían legítimas para los clientes y una vez instaladas en los sistemas objetivo, el código malicioso abrió una comunicación trasera con los servidores de los atacantes y con movimientos laterales obtuvieron una posición más sólida. |
|
NotPetya (2017) |
El ataque NotPetya se originó en Ucrania en 2017, inicialmente se creía que el mecanismo de actualización del Software M.E.Doc estaba comprometido y se utilizó una técnica similar a Mimikatz para la recolección de credenciales. Tras obtener acceso en las redes, se emplearon métodos como Pass-the-Hash (PtH), el exploit External blue, el abuso de la herramienta PsExec y métodos autoreplicantes para moverse lateralmente y propagarse rápidamente, infectando sistemas a nivel mundial y causando pérdidas de miles de millones de dólares. |
|
WannaCry (2017): |
Fue un ataque de ransomware, que explotó la vulnerabilidad Eternal blue del protocolo de la versión de bloque de windows Server 1 (SMBv1) y se propagó rápidamente por todo el mundo infectando más de 200,000 sistemas. Eventualmente, Microsoft lanzó un parche para la vulnerabilidad Eternal blue, y su impacto fue contenido. |
Consecuencias del movimiento lateral
Los sofisticados ciberataques con movimiento lateral permitieron a los atacantes dañar a las organizaciones de varias maneras, algunas de ellas son las siguientes:
Área de impacto | Descripción |
|---|---|
|
Financiero |
Pagos de rescate, multas regulatorias, pérdida de ingresos debido a tiempo de inactividad. |
|
Operativo |
Interrupción del negocio, cifrado de datos, sistemas bloqueados. |
|
Reputacional |
Pérdida de confianza de los clientes, daño a la marca, pérdida de asociaciones. |
|
Legal/Regulatorio |
Multas del GDPR, violaciones del PCI DSS, incumplimiento de la HIPAA. |
Área de impacto | Descripción |
|---|---|
|
Financiero |
Los atacantes pueden cifrar datos en múltiples sistemas y exigir un rescate por la clave de descifrado, la violación de datos resulta en multas regulatorias, el costo de la remediación es aparte y, en última instancia, pérdida de ingresos. |
|
Operativo |
Los bloqueos del sistema, las interrupciones de servicios y la pérdida de datos críticos pueden causar graves problemas operativos para las organizaciones en el día a día y, a veces, incluso durante semanas o meses. |
|
Reputacional |
Las brechas de datos y los incidentes de seguridad son pesadillas para la reputación de las organizaciones y, en consecuencia, conducen a la pérdida de clientes, daño a la marca, pérdida de asociaciones y disminución de los valores de las acciones. |
|
Legal/Regulatorio |
Las organizaciones que manejan datos personales del público general pueden enfrentar multas severas de acuerdo con leyes regionales como el Reglamento General de Protección de Datos (GDPR) de la UE, en la industria bancaria regulaciones como el Estándar de Datos para la Industria de Tarjetas de Pago (PCI DSS) y la no conformidad con HIPPA en Estados Unidos en cuanto a la información de salud de los pacientes entra en efecto en caso de violaciones de datos. |
Objetivos más comunes
Empresas y corporaciones
Las grandes organizaciones son objetivos atractivos porque a menudo poseen datos de alto valor, incluyendo información financiera, propiedad intelectual y registros de clientes.
Las instituciones financieras como bancos, firmas de inversión y procesadores de pagos son objetivos debido a su acceso directo a fondos e información financiera de los clientes.
El sector minorista y el comercio electrónico son lucrativos por diversas razones, es decir, los sistemas de punto de venta contienen información de tarjetas de crédito, las bases de datos de clientes contienen información personal y financiera y las redes de la cadena de suministro pueden permitir el acceso a organizaciones asociadas.
Gobierno e Infraestructura Crítica
Las agencias gubernamentales son objetivos de ciberdelincuentes patrocinados por estados rivales o individuales para la extracción de datos clasificados, fines de espionaje y para sabotear operaciones y servicios gubernamentales.
Sectores energéticos como las redes eléctricas, plantas de tratamiento de agua, gasoductos también son objetivo de ataques de mentes criminales con financiamiento extranjero o por mera fama. Estas instalaciones utilizan tecnologías operativas y sistemas de control industrial, requieren técnicas sofisticadas y planificación para interrumpir las operaciones.
El sector de la salud y los hospitales son objetivos de ataques para obtener datos de pacientes que pueden ser vendidos en línea; los ataques de ransomware y la denegación de servicios críticos también son comunes, ya que la información crítica en la historia clínica de los pacientes es importante en esta industria, y se ven obligados a cumplir con las demandas de los atacantes para mantenerse operativos.
PYMES y cadenas de suministro
Las pequeñas y medianas empresas (PYMEs) también son un objetivo frecuente ya que en la mayoría de los casos cuentan con defensas de seguridad más débiles y menos recursos dedicados a la ciberseguridad, convirtiéndose en peldaños para alcanzar a las empresas asociadas.
Los atacantes a menudo se dirigen a proveedores y vendedores de terceros de grandes organizaciones para obtener acceso a las organizaciones objetivo, el incidente de SolarWinds es un ejemplo de este escenario.
Entornos en la nube y fuerzas de trabajo remotas
A medida que más y más organizaciones se orientan hacia soluciones basadas en la nube, los atacantes también están dirigiendo sus esfuerzos a redes basadas en la nube y el movimiento lateral permite a los actores de amenazas desplazarse por entornos de nube multiinquilino para obtener acceso a datos sensibles almacenados en la nube.
La fuerza laboral remota de organizaciones con políticas de autenticación débiles o credenciales que utilizan VPNs, escritorios remotos y portales web basados en la nube son objetivos principales de los atacantes como puntos de entrada para moverse en redes corporativas y subsistemas.
Cuentas de alto privilegio y administradores de TI
Los administradores de sistemas y el personal de TI con Privileged Access son los principales objetivos de los atacantes para obtener movimiento lateral ilimitado en la red y permanecer sin ser detectados.
Las cuentas de servicio y las cuentas de usuario con privilegios se utilizan para diferentes aplicaciones y servicios de distintos softwares de terceros y, si son comprometidas por atacantes, pueden ser utilizadas para una infiltración profunda sin detección.
Evaluación de riesgos
La evaluación de riesgos asociada con el ataque de movimiento lateral es extremadamente importante para identificar vulnerabilidades, implementar controles de seguridad y desarrollar estrategias efectivas para prevenir, detectar y responder a cualquier intrusión potencial. Sin planificación o una evaluación exhaustiva, cualquier brecha de seguridad permanecerá sin detectar y la exposición a ataques devastadores será alta sin conocimiento.
El movimiento lateral no es un escenario atípico en la actualidad, es una táctica muy común utilizada por los atacantes para obtener acceso a activos valiosos, una vez que han vulnerado la defensa de seguridad.
La gravedad potencial del movimiento lateral es de nivel crítico porque después de una brecha inicial por accidente o atrapamiento, si los atacantes pueden moverse fácilmente por redes y subsistemas, pueden escalar rápidamente los privilegios de acceso y tomar el control total de los sistemas empresariales sin detección y pueden causar mucho daño en términos financieros o interrupción de sistemas críticos.
La dificultad de detección también es alta en caso de movimiento lateral, ya que imita la actividad de red legítima y normal utilizando cuentas comprometidas y herramientas estándar. Identificar el movimiento lateral requiere herramientas de monitoreo sofisticadas, analistas de seguridad capacitados y un profundo entendimiento de los patrones de tráfico de red.
Cómo prevenir el movimiento lateral
Los equipos de seguridad de las organizaciones deben adoptar un enfoque proactivo y estratificado para implementar medidas de seguridad de manera estratégica que prevengan, detecten y mitiguen el movimiento lateral.
Seguridad Zero Trust – Asuma que cada usuario y dispositivo es una amenaza potencial.
La seguridad de confianza cero es una filosofía de seguridad que opera bajo el principio de “nunca confiar, siempre verificar”. Implemente un estricto Identity and Access Management (IAM) mediante mecanismos de autenticación y autorización fuertes para cada usuario y dispositivos que intenten acceder a recursos. Verificación continua de usuarios, dispositivos y aplicaciones con re-autenticación y re-autorización y configuración de token de acceso con limitación de tiempo. Cree segmentación en la red para limitar y segregar el acceso de usuarios, dispositivos y aplicaciones para restringir el movimiento no detectado si un segmento está comprometido.
Autenticación Multifactor (MFA) – Bloquea inicios de sesión no autorizados.
La autenticación multifactor agrega una capa adicional de seguridad al proceso de inicio de sesión, obligando a los usuarios finales a proporcionar dos o más factores de verificación. Haga cumplir la autenticación multifactor en todos los usuarios y cuentas de servicio y agregue conciencia de contexto en este proceso para considerar la ubicación del usuario, el dispositivo y el recurso que se está accediendo durante el proceso de inicio de sesión.
Segmentación de red y microsegmentación: restringe las rutas de movimiento lateral.
La segmentación de red implica dividir las redes en segmentos distintos y aislados con acceso restringido para un conjunto específico de recursos, es decir, usuarios, dispositivos, aplicaciones. La microsegmentación lleva este enfoque al siguiente nivel al crear segmentos aún más pequeños con control granular para flujos de trabajo específicos entre recursos. Esto se puede lograr identificando activos críticos, flujo de datos y mapeando caminos de comunicación legítimos entre solo los recursos esenciales. Defina zonas de seguridad, implemente segmentación física y lógica con la ayuda de VLANs, firewalls, SDN (redes definidas por software) e implemente los privilegios mínimos para el acceso a la red.
Endpoint Detection & Response (EDR) – Identifica actividades sospechosas en dispositivos.
Las soluciones de Endpoint Detection & Response (EDR) monitorean y analizan continuamente las actividades de los endpoints, recopilan datos sobre procesos y conexiones de red, cambios de archivos y pueden generar alertas o respuestas automatizadas. Las soluciones EDR pueden analizar patrones de actividades, detectar intentos maliciosos de pass-the-hash, inyecciones de procesos remotos y uso anormal de herramientas. También proporcionan información sobre el análisis posterior a incidentes, ayudando a los equipos de seguridad a rastrear los movimientos del atacante e identificar sistemas potencialmente comprometidos.
Gestión de Información de Seguridad y Gestión de Eventos (SIEM) – Registra y detecta anomalías.
Los sistemas de Security information and Event Management (SIEM) recopilan y analizan registros de seguridad y datos de eventos de diferentes fuentes dentro de sistemas como dispositivos de red, servidores, puntos finales de aplicaciones y herramientas de seguridad para detectar patrones sospechosos e incidentes de seguridad potenciales que pueden indicar movimiento lateral y ayudar en la búsqueda de amenazas de seguridad. SIEM puede detectar y generar alertas en tiempo real basadas en Indicadores de cumplimiento (IoCs) configurados, proporcionar conocimientos forenses de intentos de inicio de sesión fallidos, tráfico de red inusual desde una ubicación o sistema específico e intentos de acceso privilegiado.
User Behavior Analytics (UBA) – Marca patrones de inicio de sesión inusuales.
El análisis de comportamiento del usuario (UBA) monitorea y establece patrones de actividad del usuario como horarios de inicio de sesión, duración, ubicación del dispositivo, uso de recursos y luego analiza cualquier desviación del patrón para señalar actividades sospechosas como el movimiento lateral. UBA asigna puntajes de riesgo a actividades anómalas, ayudando al equipo de seguridad a priorizar alertas y puede integrarse con SIEM y otras herramientas de seguridad.
Cómo Netwrix Endpoint Policy Manager ayuda a prevenir el movimiento lateral
Netwrix Endpoint Policy Manager es una solución empresarial que proporciona a las organizaciones soluciones para la gestión de privilegios de usuario en dispositivos de la organización. Esto puede ayudar a prevenir el movimiento lateral y los ataques de ransomware porque, incluso después de obtener el acceso inicial, los atacantes encuentran un sistema completamente bloqueado sin puntos ni dirección para moverse y obtener más acceso.
Las políticas de Netwrix Endpoint Policy Manager pueden evitar que los usuarios instalen cualquier software que no sea el software esencial permitido, gestionar cómo los usuarios pueden usar almacenamiento extraíble y evitar que cambien las configuraciones de seguridad. Puede restringir la interacción del usuario final con aplicaciones, configuraciones de navegadores y applets de Java, impedirles que las reconfiguren, lograr el cumplimiento y reducir la vulnerabilidad asegurándose de que la configuración de las políticas de grupo esté configurada correctamente.
Estrategias de detección, mitigación y respuesta
Señales de advertencia temprana de un ataque
Mantenga un ojo en las actividades de inicio de sesión inusuales desde ubicaciones desconocidas o fuera del horario laboral habitual. Un aumento repentino en los intentos fallidos de inicio de sesión y un aumento en el tráfico de la red pueden indicar ataques de fuerza bruta, comunicación de malware, actividad de botnet o movimiento lateral en curso. Los intentos de acceder a servicios críticos o servidores backend, especialmente desde direcciones IP desconocidas y los intentos de transferencia de grandes datos, requieren una respuesta inmediata para investigar anomalías.
Pasos inmediatos de respuesta
Comience a aislar los sistemas afectados desconectándolos de la red principal, mediante reglas de firewall o desconectando físicamente los cables, deshabilite las credenciales comprometidas o fuerce el restablecimiento de contraseñas y habilite MFA en las cuentas comprometidas. Examine los registros en los sistemas comprometidos, firewalls, registros de autenticación y analice las actividades de los endpoints para rastrear los movimientos de los atacantes. Utilice herramientas forenses especializadas para analizar la presencia de malware, puertas traseras o cualquier mecanismo de persistencia.
Estrategias de mitigación a largo plazo
Implemente estrategias de mitigación a largo plazo como el principio de privilegio mínimo, asegurando que los usuarios solo tengan acceso a los recursos que son necesarios para realizar sus tareas y revise regularmente los permisos de acceso. Realice pruebas de penetración rutinarias para identificar vulnerabilidades que puedan ser aprovechadas para ataques potenciales y abórdelas de manera rápida con parches y cambios de configuración.
Impacto específico del sector
Industria | Impacto |
|---|---|
|
Sanidad |
Fugas de datos de pacientes, ransomware dirigido a sistemas hospitalarios. |
|
Finanzas |
Fraude bancario, transferencias no autorizadas, amenazas internas. |
|
Retail |
Malware de punto de venta, brechas de proveedores que afectan las cadenas de suministro. |
Industria | Impacto |
|---|---|
|
Sanidad |
Los ciberatacantes en la industria de la salud comúnmente buscan datos de pacientes como historial médico, diagnósticos, planes de tratamiento y detalles personales, como resultado, los institutos de salud no solo pueden enfrentar problemas financieros sino también problemas regulatorios como el incumplimiento de HIPPA, lo que puede resultar en sanciones legales y financieras. Los ataques de ransomware pueden interrumpir servicios críticos como el acceso a registros de pacientes e informes de laboratorio en ERP, las configuraciones de dispositivos críticos pueden ser alteradas para malfuncionar y forzar al instituto a pagar en la urgencia de restauración del sistema. |
|
Finanzas |
En el sector financiero, los atacantes suelen explotar vulnerabilidades en los sistemas de banca en línea para realizar transferencias de fondos no autorizadas, despliegan técnicas de phishing para engañar a los empleados y que revelen información sensible y luego pueden usarla para obtener acceso a la red. Esto no solo resulta en pérdidas financieras sino también en multas regulatorias y escrutinio por parte de los organismos reguladores debido a medidas de seguridad débiles. En el caso de instituciones financieras como los mercados de valores o bancos de inversión, el acceso no detectado a información sensible puede llevar a operaciones con información privilegiada, manipulación de los precios de las acciones y puede ser difícil de distinguir entre actividad legítima y maliciosa debido a la escala de las transacciones. |
|
Retail |
El significado del movimiento lateral en el contexto de la ciberseguridad para la industria minorista es ayudar a los atacantes a violar múltiples sistemas de Punto de Venta (POS) a lo largo de la organización, recopilar información de la tarjeta de pago de los clientes y esto conduce a violaciones de datos a gran escala. Las técnicas de movimiento lateral pueden ser utilizadas para explotar los sistemas de la cadena de suministro, apuntando a proveedores y organizaciones asociadas que pueden ser utilizadas para una mayor infiltración con el fin de interrumpir operaciones o extraer datos. |
Evolución de los ataques y tendencias futuras
Al igual que cualquier otra tecnología, los ciberataques están evolucionando y adoptando técnicas sofisticadas para permanecer persistentes y navegar por las redes sin ser detectados.
Movimiento lateral impulsado por IA: Atacantes que utilizan IA para reconocimiento automatizado y escalada de privilegios más rápida.
Los atacantes están utilizando Inteligencia Artificial y algoritmos de aprendizaje automático para automatizar diversas etapas del movimiento lateral con el fin de imitar comportamientos legítimos de usuarios, técnicas de reconocimiento complejas y más rápidas para encontrar explotaciones de software y de red con una escalada de privilegios fácil sin ser detectados.
Ataques basados en la nube: Movimiento lateral dentro de entornos en la nube y redes híbridas.
Con la infraestructura trasladándose a la nube o implementaciones híbridas, los atacantes también están apuntando a infraestructuras en la nube como AWS, Azure y GCP. En estos entornos, la mala configuración, credenciales o tokens de acceso robados, API’s vulnerables, políticas débiles de Identity and Access Management (IAM) son puntos de entrada fáciles y para moverse alrededor de los servicios en la nube.
Deepfake Phishing: Impersonaciones generadas por IA utilizadas para robar credenciales.
Los deepfake generados por IA, como mensajes de audio o video, se utilizan para suplantar a autoridades superiores y engañar a los empleados para que compartan credenciales o aprueben acceso autorizado a servicios o recursos críticos.
Explotación de la Cadena de Suministro: Atacantes se mueven lateralmente a través de proveedores tercerizados.
Este enfoque implica obtener acceso a organizaciones objetivo a través de recursos comprometidos de un proveedor externo que tiene acceso a la organización objetivo, como actualizaciones de software. Una vez que se establece una puerta trasera en la organización objetivo, los atacantes pueden moverse lateralmente en la red y estos ataques son prácticamente silenciosos ya que la organización objetivo tiene menos control sobre el entorno del proveedor.
Estadísticas Clave & Infografías
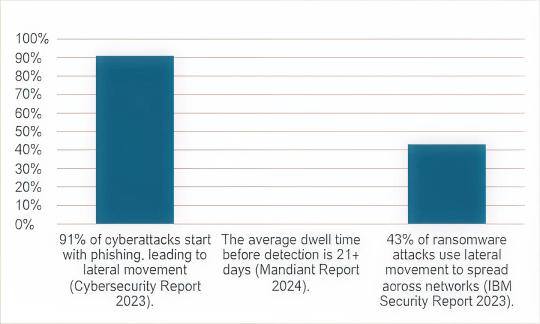
Según informes de ciberseguridad, el 91% de los puntos de inicio de ciberataques son técnicas de phishing, engañando a individuos para que revelen credenciales o descarguen malware sin saberlo.
Según el informe de Mandiant de 2024, el tiempo promedio de permanencia de los atacantes moviéndose por la red sin ser detectados es de más de 21 días, lo cual es alarmante ya que algunas de las técnicas de exfiltración de datos no dejan rastros y este intervalo proporciona tiempo suficiente para interrumpir cualquier servicio o sistema crítico.
El informe de seguridad de IBM de 2023 sugiere que casi la mitad de los ataques (43%) utilizan técnicas de movimiento lateral para amplificar el impacto y alcanzar tantos sistemas como sea posible y repositorio de datos antes de iniciar el ataque final.
Reflexiones finales
Hemos discutido la definición de movimiento lateral y las diferentes fases en detalle, como el acceso inicial con ataque de phishing o archivos adjuntos infectados, Reconocimiento de segmentos de red después de obtener acceso inicial, escalando privilegios utilizando vulnerabilidades conocidas para obtener un control más amplio del sistema, movimiento lateral para encontrar repositorios de datos críticos y ejecutar el ataque final para extraer datos sensibles y perturbar servicios críticos a cambio de rescate o daño permanente. Los ataques de movimiento lateral se centran de manera diferente en varias industrias, por ejemplo, en instituciones financieras los atacantes buscan transferencias de fondos no autorizadas, fraudes con tarjetas de crédito y manipulación de datos sensibles para el comercio de información privilegiada. En la industria de la salud, el objetivo es obtener datos de pacientes o desplegar malware para obtener rescate, en negocios minoristas los atacantes despliegan código malicioso en terminales de punto de venta para extraer datos de clientes o apuntan a pequeñas empresas para obtener acceso a sus empresas asociadas.
Un enfoque proactivo con una combinación de estrategias y herramientas es la mejor manera de prevenir y detectar el movimiento lateral en caso de que los atacantes obtengan acceso a un segmento de la red. Implemente autenticación multifactor para cada usuario y cuentas de servicio con segregación de red y empleando el principio de acceso de mínimos privilegios. Despliegue soluciones de End point detection and response (EDR), monitoreo regular de intentos fallidos de inicio de sesión, flujos de datos inusuales, análisis exhaustivo semanal de registros y pruebas regulares de diferentes configuraciones para escenarios de escalada de privilegios.
Preguntas frecuentes
Compartir en
Ver ataques de ciberseguridad relacionados
Abuso de permisos de aplicaciones Entra ID – Cómo funciona y estrategias de defensa
Modificación de AdminSDHolder – Cómo funciona y estrategias de defensa
Ataque AS-REP Roasting - Cómo funciona y estrategias de defensa
Ataque Hafnium - Cómo funciona y estrategias de defensa
Ataques DCSync explicados: Amenaza a la seguridad de Active Directory
Ataque Golden SAML
Entendiendo los ataques de Golden Ticket
Ataque de Cuentas de Servicio Administradas por Grupo
Ataque DCShadow – Cómo funciona, ejemplos del mundo real y estrategias de defensa
ChatGPT Prompt Injection: Comprensión de riesgos, ejemplos y prevención
Ataque de extracción de contraseñas de NTDS.dit
Ataque de Pass the Hash
Explicación del ataque Pass-the-Ticket: Riesgos, ejemplos y estrategias de defensa
Ataque de Password Spraying
Ataque de extracción de contraseñas en texto plano
Explicación de la vulnerabilidad Zerologon: Riesgos, Explotaciones y Mitigación
Ataques de ransomware a Active Directory
Desbloqueando Active Directory con el ataque Skeleton Key
Ataque de Kerberoasting – Cómo funciona y estrategias de defensa
Ataques de Hombre en el Medio (MITM): Qué son y cómo prevenirlos
¿Por qué es PowerShell tan popular entre los atacantes?
4 ataques a cuentas de servicio y cómo protegerse contra ellos
Cómo prevenir que los ataques de malware afecten a su negocio
¿Qué es Credential Stuffing?
Comprometiendo SQL Server con PowerUpSQL
¿Qué son los ataques de Mousejacking y cómo defenderse de ellos?
Robo de credenciales con un Proveedor de Soporte de Seguridad (SSP)
Ataques de Rainbow Table: Cómo funcionan y cómo defenderse de ellos
Una mirada exhaustiva a los ataques de contraseñas y cómo detenerlos
Reconocimiento LDAP
Eludir MFA con el ataque Pass-the-Cookie
Ataque de Silver Ticket
